GitHub Advanced Security Permissions Chart
An access requirements/permissions comparison between various roles in GitHub Enterprise and GitHub Advanced Security, such as what users with Write access to the repository get vs. what requires elevated privileges
Overview
I have several posts discussing GitHub Advanced Security, but practically a question that I get often is: “Who can access the alerts on each repository?”
I hope to solve that with this permissions / access requirements chart!
See also: GitHub Advanced Security Feature Comparison
Access requirements for security features
This chart is loosely based on the one from GitHub, with a few additions, modifications, and clarifications.
| Feature | Read[1] | Write,Mntn [2] | Admin | Sec. Mgr | Org Owner |
|---|---|---|---|---|---|
| Receive Dependabot alerts | ✔️ | ✔️ | ✔️ | ✔️ | |
| Dismiss Dependabot alerts | ✔️ | ✔️ | ✔️ | ✔️ | |
| Designate others to receive security alerts | ✔️ | ✔️ | ✔️ | ||
| Create security advisories | ✔️ | ✔️ | ✔️ | ||
| Manage access to GHAS features in the repo | ✔️ | ✔️ | ✔️ | ||
| Enable the dependency graph | ✔️ | ✔️ | ✔️ | ||
| View dependency reviews | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| View code scanning alerts on pull requests | ✔️ | ✔️ | ✔️ | ✔️ | ✔️ |
| Manage code scanning alerts | ✔️ | ✔️ | ✔️ | ✔️ | |
| View secret scanning alerts in a repository | ⚠️[3] | ✔️ | ✔️ | ✔️ | |
| Manage secret scanning alerts | ⚠️[3] | ✔️ | ✔️ | ✔️ | |
| Access to the org’s security overview | ✔️[4] | ✔️[4] | ✔️ | ✔️ | |
| Access to the enterprise’s security overview | ✔️[5] | ✔️[5] | |||
| Manage GHAS features at org level | ✔️ | ✔️ | |||
| Designate Security Managers | ✔️ | ||||
| Read access to repo(s) | ✔️ | ✔️ | ✔️ | ✔️[6] | ✔️ |
| Write access to repo(s) | ✔️ | ✔️ | ✔️ |
Notes:
- [1] Read and Triage have the same rights for security features
- [2] Write and Maintain have the same rights for security features
- [3] Repository writers and maintainers can only see secret alert information for their own commits, but only as a direct link to the secret scanning alert sent via email ⚠️
- [4] Now that the org-level security overview is available to all Enterprise users, org members can see consolidated results of repositories that they can see alerts for (e.g., write for CodeQL and Dependabot, admin for secrets)
- [5] In the enterprise-level security overview level, one would see organizations where they are added as an org owner or security manager - enterprise owners must join an organization as an owner to see alerts
- [6] Security managers get read-only access to every repository in the organization
- This chart primarily focuses on GitHub Enterprise Cloud, but note that Advanced Security is available for GitHub Enterprise Server 3.0 or higher. There may be slight differences in the features available for GitHub Enterprise Server based on the version
Granting access to security alerts
Security alerts for a repository are visible to people with admin access to the repository and, when the repository is owned by an organization, organization owners. You can also give additional teams and people access to the alerts.
When adding users to be able to view security alerts, there is a bit of text that explains (emphasis mine):
Admins, users, and teams in the list below have permission to view and manage code scanning, Dependabot, or secret scanning alerts. These users may be notified when a new vulnerability is found in one of this repository’s dependencies and when a secret or key is checked in. They will also see additional details when viewing Dependabot security updates. Individuals can manage how they receive these alerts in their notification settings.
Note: Organization owners and repository administrators can only grant access to view security alerts, such as secret scanning alerts, to people or teams who have write access to the repo.
Custom Repository Roles
Organization administrators can create Custom Repository Roles to customize and fine-tune different permission sets that repository administrators can grant. For example, I want to create a role that allows users to have Write access AND be able to view/dismiss Dependabot Alerts:
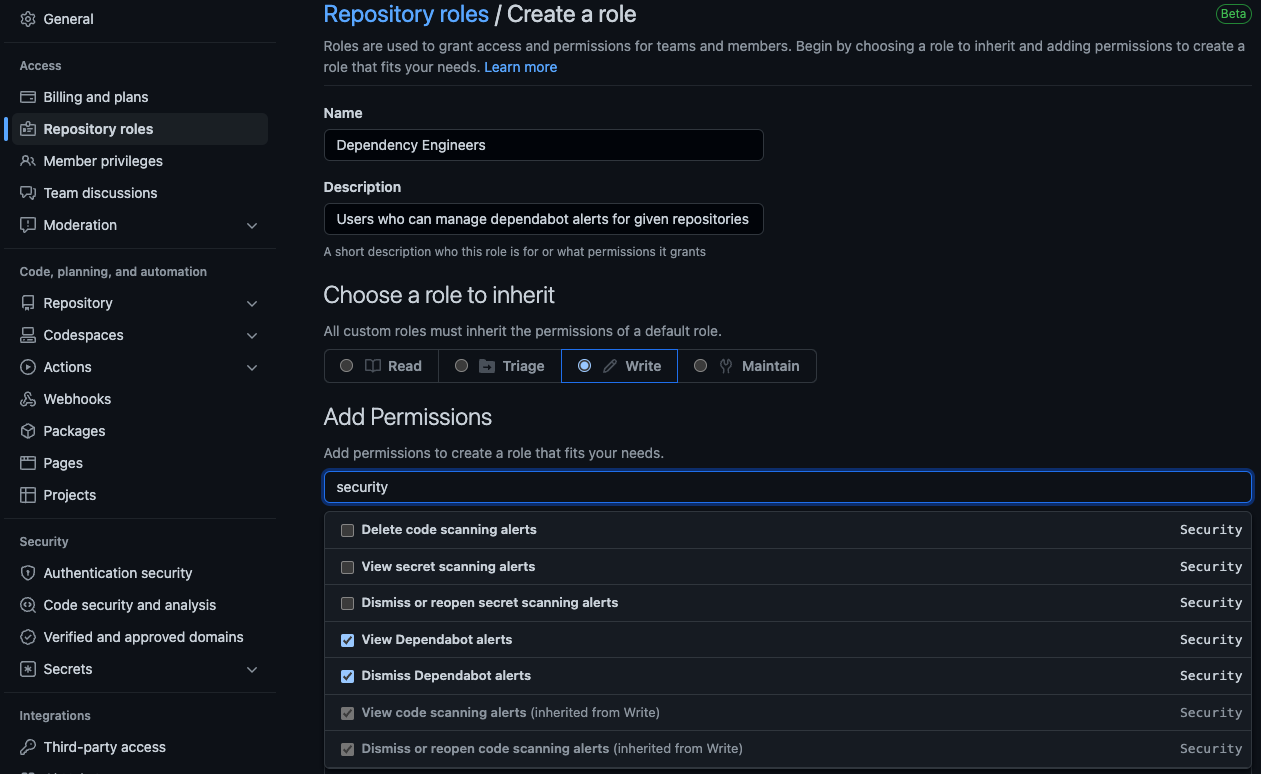 Custom repository roles - creating a custom role to allow viewing/managing of Dependabot alerts
Custom repository roles - creating a custom role to allow viewing/managing of Dependabot alerts
Note that there is currently a maximum of 3 custom roles that can be created in the organization.
Changelog
| Date | Note |
|---|---|
| Apr 26 2023 | Write and Maintain can view/manage Dependabot alerts now (GHES 3.9+) |
| Oct 11 2022 | Removing Beta from Security Overview for the Org, Security Overview is available to all GitHub Enterprise customers, Consolidated Read/Triage and Write/Maintain since they have the same security permissions |
| Mar 11 2021 | Adding section about security alerts |
| Mar 08 2021 | Initial post |