Exporting GitHub Actions Dependency Data for Your Organization
Compare three methods for getting GitHub Actions usage data for organization governance: The Dependency Insights view in GitHub, @stoe/action-reporting-cli, and my custom SBOM script
Overview
In my previous post on GitHub Actions Allow Lists, I discussed how to manage which Actions your organization can use through configuration as code. But before you implement an allow list, you might ask: What Actions are my organization actually using?
Whether you’re building an allow list, conducting a security audit, hunting down deprecated versions, or just want to know what’s actually running in your CI/CD pipelines, you need visibility into which GitHub Actions are being used across your repositories.
This post covers three different approaches for getting that data:
- GitHub’s Dependency Insights - Native viewing capabilities (but no export)
- @stoe/action-reporting-cli - Full-featured CLI tool with multiple export formats (csv, json, or markdown)
- My Custom Software Bill of Materials (SBOM) Script - Lightweight shell script for automated reporting on Actions usage with capabilities to resolve SHAs to tag versions (exports to csv or markdown)
If you want to skip ahead, use the links above to jump to any of these methods.
Why This Matters
Let’s quickly recap why Actions usage reporting is important:
- Security & Compliance: Know your third-party dependencies and assess potential security risks
- Governance Planning: Make informed decisions about which Actions to allow or restrict
- Dependency Management: Track Action versions and identify outdated or deprecated Actions (like
actions/upload-artifactandactions/download-artifactversions earlier thanv4) - Supply Chain Visibility: Build a Software Bill of Materials (SBOM) for your CI/CD pipeline
Three Methods for Getting Actions Usage Data
Method 1: GitHub’s Dependency Insights (View-Only)
GitHub’s Dependency Insights feature provides visibility into dependencies used across your organization. You’ll need to filter specifically for GitHub Actions to see only Actions usage:
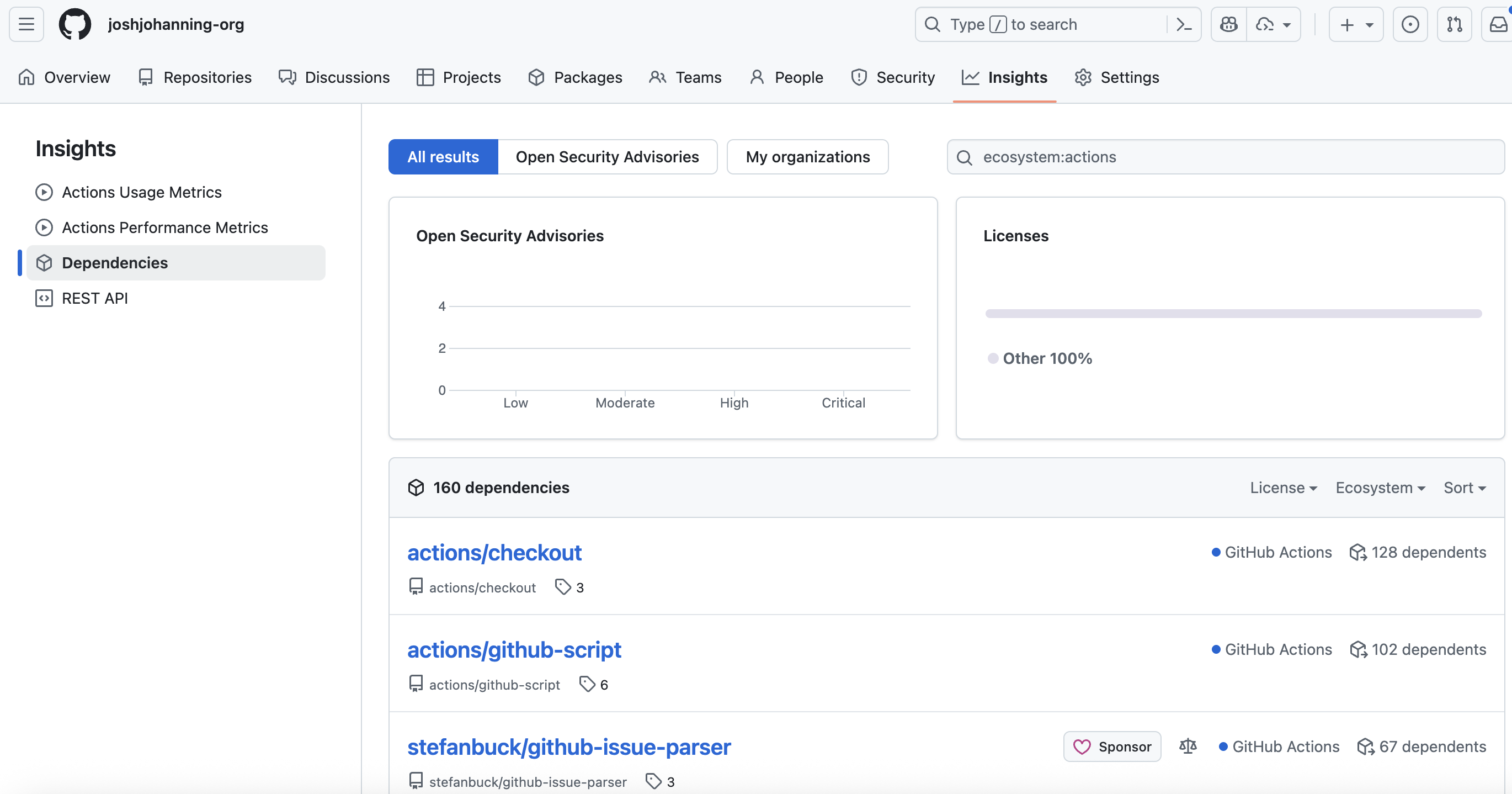
 GitHub’s native Dependency Insights showing Actions usage across an organization
GitHub’s native Dependency Insights showing Actions usage across an organization
While this view provides excellent visibility, it has limitations:
- No export functionality: You can view the data but not export it for further analysis
- Limited filtering: Basic filtering options compared to programmatic approaches
- No historical data: Shows current state but lacks trend analysis
That’s where the automated tools come in handy - they give you more control and can export data for deeper analysis.
Method 2: @stoe/action-reporting-cli (Full-Featured Solution)
The @stoe/action-reporting-cli tool by Stefan Stölzle provides comprehensive GitHub Actions reporting capabilities.
See my automated workflow implementation that runs this tool on a schedule and save the outputs back to the repository.
Key features:
- Multiple export formats: CSV, JSON, and Markdown outputs
- Comprehensive data collection: in addition to what actions are used, can also report on secrets, variables, permissions, listeners (workflow triggers), and/or runners
- Flexible scope options: run for an entire enterprise (can’t use GitHub App though), organization, or a single repository
- Advanced filtering: exclude GitHub-created actions, unique actions reporting, and ability to exclude archived and forked repositories
Sample output:
Full example output -
@stoe/action-reporting-cli:json,md,csv
Sample Usage:
1
2
3
4
5
6
7
8
9
# Organization-wide analysis with all data types
npx @stoe/action-reporting-cli
--owner my-org
--all
--exclude
--unique both
--csv ./reports/actions.csv
--json ./reports/actions.json
--md ./reports/actions.md
Method 3: Custom SBOM Script (My Lightweight Solution)
The approach I’ve developed focuses on SBOM-style reporting with automated GitHub workflows. The script is located in my github-misc-scripts repository.
See my automated workflow implementation that runs this tool on a schedule and save the outputs back to the repository.
Key features:
What makes this script useful:
- Usage frequency counts: Shows how many times each Action is used across the organization in an SBOM-like report
- Version distribution: Identifies which versions of Actions are most commonly used
- SHA resolution: Automatically resolves commit SHAs to readable tag versions when possible
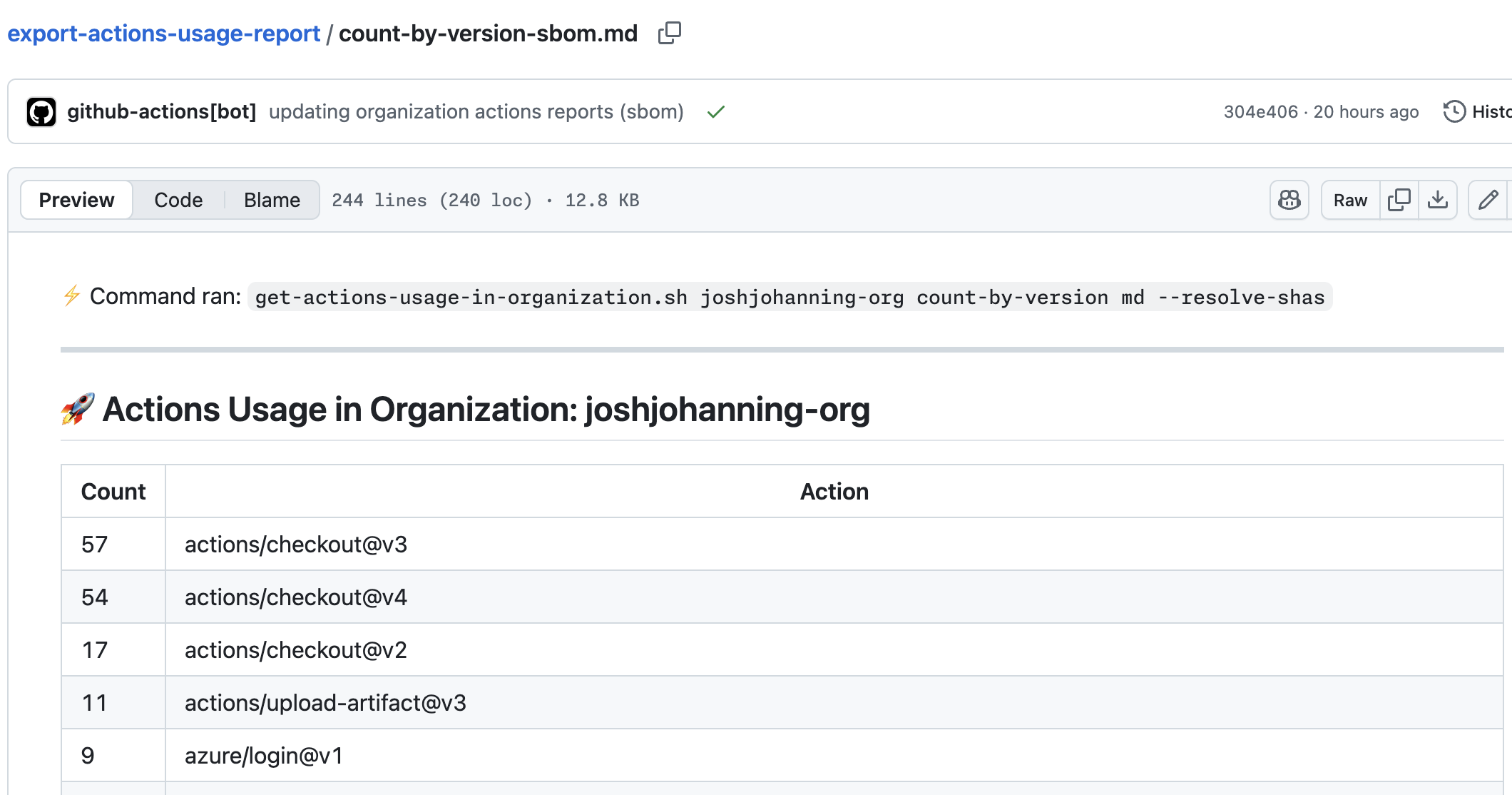
Sample Output - Count by Action:
Sample Output - Count by Version:
Sample Usage:
1
2
3
4
5
# different options
./get-actions-usage-in-organization.sh joshjohanning-org count-by-version csv > output.csv
./get-actions-usage-in-organization.sh joshjohanning-org count-by-action md > output.md
./get-actions-usage-in-organization.sh joshjohanning-org count-by-version md --resolve-shas > output.md
./get-actions-usage-in-organization.sh joshjohanning-org count-by-action md --dedupe-by-repo > output.md
Need single repository analysis? I also have a repository-level version of this script that works the same way but analyzes just one repository instead of an entire organization.
Choosing the Right Method
- Use GitHub Dependency Insights first to get familiar with your organization’s usage patterns
- Use @stoe/action-reporting-cli for comprehensive analysis with flexible export options, and especially if you want to report on other things like secrets, variables, permissions, listeners (workflow triggers), and/or runners (For implementing, see: Using the Pre-Built Workflows section)
- Use my custom SBOM script if you want usage statistics and the ability to resolve SHAs to tag versions (For implementing, see: Using the Pre-Built Workflows section)
Using the Pre-Built Workflows
To implement these solutions in your organization:
- Fork or copy the export-actions-usage-report repository
- If you fork it, make sure to enable Actions for the forked repository to allow the scheduled job to run
- Set up GitHub App authentication:
- Create a GitHub App with the following permissions:
- Repository permissions: “Actions” (Read) - to read workflows and their usage (for
@stoe/action-reporting-cli) - Repository permissions: “Contents” (Read) - to access SBOM data via dependency graph (for my custom SBOM script)
- Repository permissions: “Actions” (Read) - to read workflows and their usage (for
- Install the app on your organization granting it access to all repositories
- Add the App ID as a repository variable (
APP_ID) - Add the private key as a repository secret (
PRIVATE_KEY) - You can use a personal access token, but a GitHub app has a higher rate limit
- See my post on GitHub Apps for detailed instructions on creating and configuring a GitHub App
- Create a GitHub App with the following permissions:
- Customize the workflows if needed (different schedule, additional output formats, etc.)
The workflows will automatically:
- Run on a weekly schedule (or manually triggered)
- Generate usage reports using both
@stoe/action-reporting-cliand my custom SBOM script - Commits results back to the repository to be able to track changes over time
- Additionally, pushes results as workflow job summaries
Summary
Having visibility into your organization’s GitHub Actions usage is essential for security, managing dependencies, and making informed decisions about your CI/CD pipelines. While GitHub’s native Dependency Insights provide a good starting point, automated export solutions offer the flexibility and depth needed for comprehensive and historical analysis.
Whether you’re implementing an Actions allow list, conducting security audits, or just wanting better visibility into your CI/CD dependencies, these tools provide the foundation for data-driven decision making.
🚀 Ready to get started? Check out the export-actions-usage-report repository and start building your Actions usage reporting today!