GitHub: Block Pull Requests if a Vulnerable Dependency is Added
Block Pull Requests in GitHub if you add a vulnerable dependency/package version
Overview
GitHub has added a new Dependency Review action to help keep vulnerable dependencies out of your repository! One of the complaints with the way Dependabot Security Alerts works in GitHub is that it only works from the default branch. As a result, you aren’t alerted that you are adding a vulnerable package until after you have already merged to the default branch. The previous solution to this was the Dependency Review (rich diff) in a pull request, but this was slightly hidden and there was no enforcement capabilities.
Note that the new Dependency Review action still requires a GitHub Advanced Security license, as mentioned in the GitHub Changelog blog post:
The dependency review action is available for use in public repositories. The action is also available in private repositories owned by organizations that use GitHub Enterprise Cloud and have a license for GitHub Advanced Security.
Dependency Review Action
The action is relatively simple (no inputs as of yet) - and here’s some additional documentation.
1
2
3
4
5
6
7
8
9
10
11
name: 'Dependency Review'
on: [pull_request]
jobs:
dependency-review:
runs-on: ubuntu-latest
steps:
- name: 'Checkout Repository'
uses: actions/checkout@v3
- name: 'Dependency Review'
uses: actions/dependency-review-action@v1
Results
To try this at home, you can attempt to "tar": "2.2.2" to the dependencies section of your package.json file. This will cause the action to fail since there are several vulnerabilities in this version of tar:
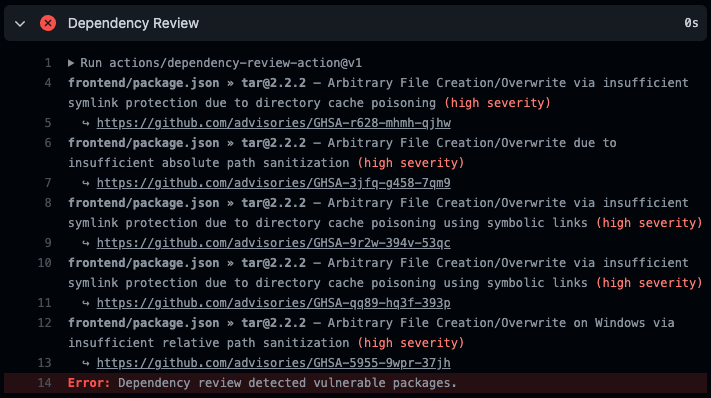 Dependency Review Action preventing a pull request with a vulnerable dependency added
Dependency Review Action preventing a pull request with a vulnerable dependency added
I think this is much better than the prior option for finding/preventing vulnerable dependencies in a pull request:
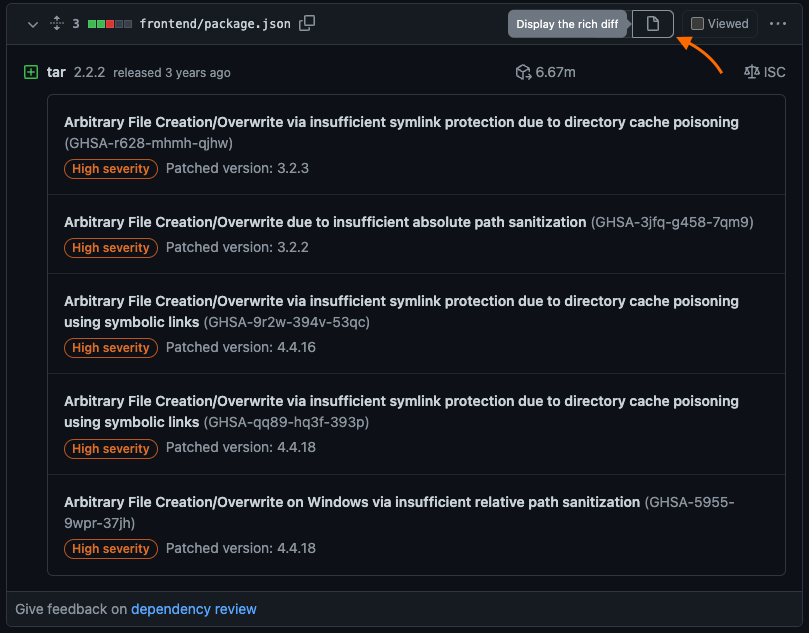 The previous option for dependency review in a pull request (rich diff)
The previous option for dependency review in a pull request (rich diff)
Making this a required status check
How To
To make this a required status check on the pull request, follow these instructions:
- The first thing you need is a public repository (GHAS is free for public repos) or a private repository with the GitHub Advanced Security license enabled
- Under the Settings tab in the repository, navigate to Branches
- Create a branch protection rule for your default branch - check the ‘Require status checks to pass before merging’ box
- Add the dependency review job as a status check - in the example above, it’s
dependency-review- If you don’t see the
dependency-reviewto add as a status check to the branch protection, it won’t appear as an option until you initiate at least one PR on the repository that triggers this job.
- If you don’t see the
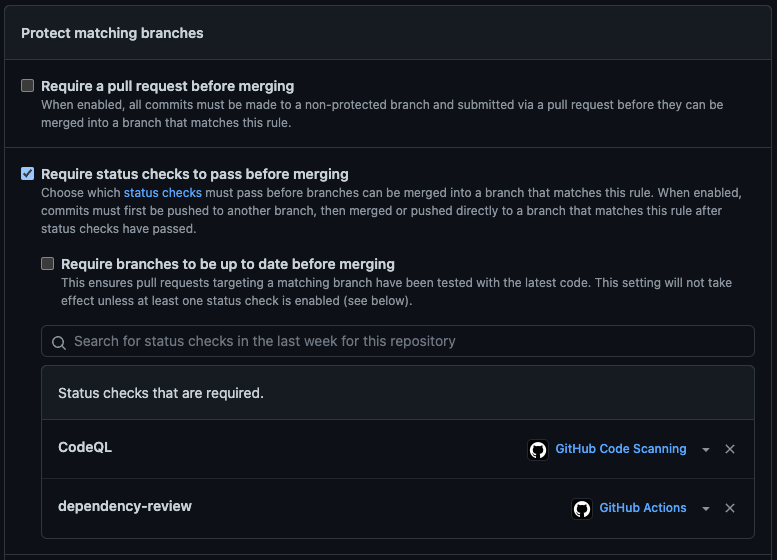 Branch Protection Policy with the dependency-review status check configured
Branch Protection Policy with the dependency-review status check configured
Summary
This new Dependency Review action uses the dependency review API endpoint to determine if you are adding a new vulnerable package version to your codebase. It doesn’t catch/block if there are any vulnerable dependencies, only dependencies added/modified in the pull request.